 TECHNOLOGY
TECHNOLOGY
ADFS (Active Directory Federation Services) is a function included in Windows Server which provides access identification solution. It allows browser clients inside and outside local network gain access to web-applications based on Single-Sign-On technology (SSO). ADFS makes this by securely sharing digital identities and entitlement rights (or Claims) among partners bounded with federation relationship.
ADFS services are closely integrated with Active Directory. ADFS retrieves user attributes from Active Directory and authenticates users in Active Directory. Besides ADFS supports Integrated Windows Authentication.
As a standard for interaction of federation components, application subsystems (relying parties) and client applications WS-Federation specification is selected. This specification is included into WS-* protocol stack developed by industrial consortium involving Microsoft and is based on other protocols of this stack such as WS-Security.
For interaction of clients and server components HTTPS is used.
ADFS is a component of Microsoft Windows Server platform providing Security Token Service (STS) according to WS-Trust and WS-Federation specifications. Security Token Service uses Active Directory to authenticate users and to store information about them.
The main operations of STS are following:
- Primary user authentication
- Security token issue
- Security token validation
- Security token renewal
- Security token cancellation
Security token is issued by STS on successful user authentication. Security token is definitely linked with the user and positively identifies application user. At the same time it is a unified format for transferring user data to application. For identification user can use:
- User name and password
- User certificate
Security token meets SAML specification (SAML Token) which is based on XML and defines token syntax and structure. This format is extensible that allows forming token according to requirements of application, access to which is performed. Security token is encrypted and signed by Security Token Service that has issued it to provide token identity and consistency and confidentiality of data being transferred in token. Token validity period and field of use are limited. Security token contains information about user as a set of claims which are used by application to create user context (also for authorization and personalization).Application or Relying Party in ADFS is an application system (web-application or web-service), which uses external authentication service giving credence to authenticate users to it and is a consumer of security tokens which are issued to users being authenticated by STS. Relying Party uses security token included in user request to application to create user context. For Relying Parties located in one security domain, that is having trust relationship with common Security Token Service, Single-Sign-On point is provided.
While accessing web-application following ADFS-related messages are sent:
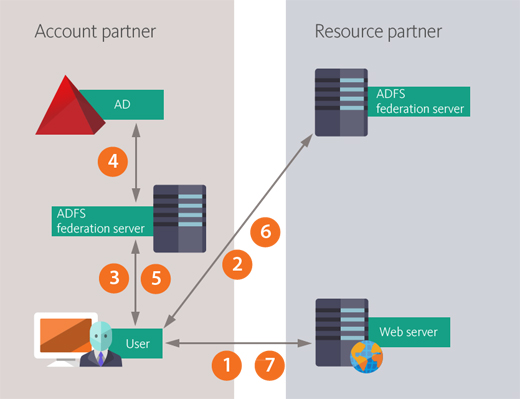
- Browser user tries to access application of web-server. ADFS agent finds out that the user was not authenticated in ADFS and redirects him to federation server of resource provider.
- At this stage known as defining home area, browser user gives information about his domain to federation server of resource provider. Home domain is a location where user identity is defined and maintained, in other words, it is user identity provider. At the first connection to web-application user sends such data as identity provider name or e-mail address. At subsequent connections federation server of resource provider finds this data in cookie-file transferred by the user. Depending on data transferred during defining home area process federation server of resource provider redirects user’s browser to federation server of identity provider for authentication.
- Browser user is authenticated in federation server of his authentication provider using his AD account and corresponding credentials.
- Federation server of authentication provider validates user credentials in AD. If the validation is finished successfully, then the server generates authentication cookie-file and security token of ADFS.
- Federation server of authentication provider issues security token and redirects user’s browser as well as security token and cookie-file to federation server of resource provider.
- Federation server of resource provider transforms request located in security token into a set of requests recognized by web-application located in resource provider and adds them into new security token. This process is known as request transformation. Federation server also generates authentication cookie-file and redirects browser user together with new security token and authentication cookie-file to ADFS agent of web-application. The agent checks authentication cookie-file, extracts request from security token and sends it to web-application.
- Web-application interprets requests during authentication process and sends corresponding web-materials to user’s browser.
Many companies are interested in possibility of data exchange with trusted external users via Internet. It is convenient for users to access resources using their own accounts without creating accounts in foreign system. However access is required only for authenticated users.
In many organizations Active Directory serves as a primary identity storage and authentication service. By using Active Directory forest trusts can be created between two or more forests to provide access to resources located in different departments or organizations.
However in some cases forest trusts are not viable type of relationship. For instance, access to resources located in different organizations may need to be limited to only small subset of users and to be denied to other forest members. Just in these cases ADFS is a perfect substitution of trust relationship of Active Directory.
Here you can find additional information about described technology and its implementation peculiarities.
